FortiEDR
Advanced attacks can take just minutes, if not seconds, to compromise the endpoints. First-generation endpoint detection and response (EDR) tools simply cannot keep pace. They require manual triage and responses that are not only too slow for fast moving threats but they also generate a huge volume of indicators that burden already overstretched security teams. Further, legacy EDR tools drive up the cost of security operations and can slow processes, negatively impacting business.
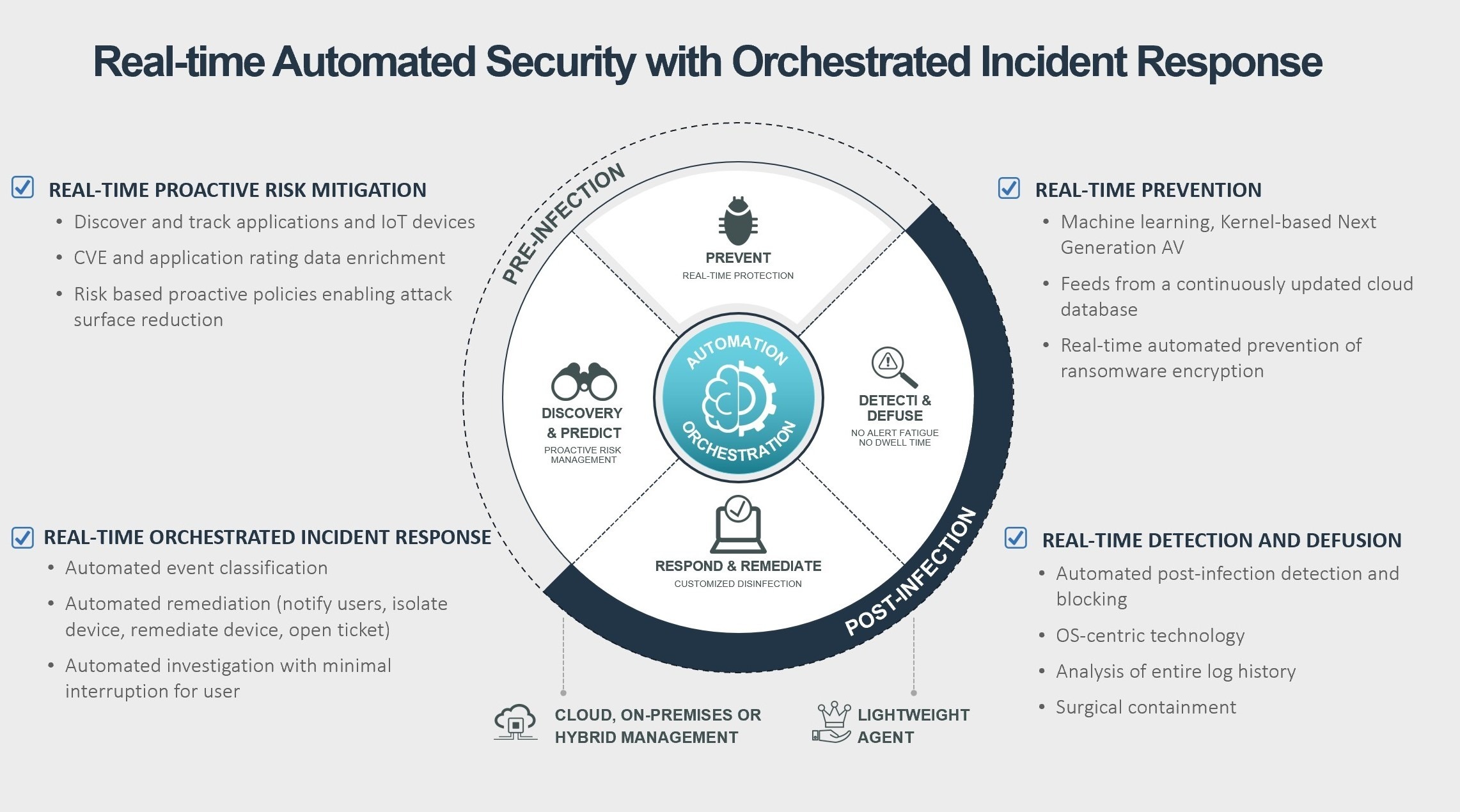
FortiEDR delivers advanced, real-time threat protection for endpoints both pre- and post-infection. It proactively reduces the attack surface, prevents malware infection, detects and defuses potential threats in real time, and can automate response and remediation procedures with customizable playbooks. FortiEDR helps organizations stop breaches in real-time automatically and efficiently, without overwhelming security teams with a slew of false alarms or disrupting business operations.
FortiEDR Features and Specifications
Discovery with proactive attack surface risk mitigation
FortiEDR delivers the most advanced automated attack surface policy control with vulnerability assessments and IoT security that allows security teams to:
- Discover and control rogue devices (e.g., unprotected or unmanaged devices) and IoT devices
- Track applications and ratings
- Discover and mitigate system and application vulnerabilities with virtual patching
- Reduce the attack surface with risk-based proactive policies
Next-generation antivirus (NGAV)
FortiEDR uses a machine learning antivirus engine to stop malware pre-execution. This cross-OS NGAV capability is configurable and comes built into the single, lightweight agent, allowing users to assign anti-malware protection to any endpoint group without requiring additional installation.
- Enable machine learning, kernel-based NGAV
- Enrich findings with real-time threat intelligence feeds from a continuously updated cloud database
- Protect disconnected endpoints with offline protection
- USB device control
Real-time and automated breach protection
FortiEDR detects and defuses fileless malware and other advanced attacks in real time to protect data and prevent breaches. As a soon as FortiEDR detects suspicious process flows and behaviors, it immediately defuses the potential threats by blocking outbound communications and access to the file system from those processes if and once requested. These steps prevent data exfiltration, command and control (C&C) communications, file tampering, and ransomware encryption. At the same time FortiEDR backend continues to gather additional evidence, enrich event data and classify the incidents.FortiEDR surgically stops data breach and ransomware damage in real time, automatically allowing business continuity even on already compromised devices.
- Leverage OS-centric detection, highly accurate in detecting stealthy infiltrated attacks, including memory based and “living off the land” attacks
- Stop breaches in real time and eliminate threat dwell time
- Achieve analysis of entire log history
- Prevent ransomware encryption, file, and registry tempering
- Continuously validate classification of threats
- Enhance signal to noise ratio and eliminate alert fatigue
Orchestrate incident response with customizable playbooks
Orchestrate incident response operations using tailor-made playbooks with cross environment insights. Streamline incident response and remediation processes, manually or automatically roll back malicious changes done by already contained threats—on a single device or on devices across the environment.
- Automate incident classification and enhance the signal-to-alert ratio
- Standardize incident response procedures with playbook automation
- Optimize security resources by automating incident response actions such as removing files, terminating malicious processes, reversing persistent changes, notifying users, isolating applications and devices, and opening tickets
- Enable contextual-based incident response using incident classification and the subjects of the attacks, (e.g., endpoint groups)
- Gain full visibility of the attack chain and malicious changes with patented code tracing
- Automate cleanup and roll back malicious changes while preserving system uptime
- Optional managed detection and response (MDR) service can supplement a SOC
Guided interface with data enrichment
FortiEDR automatically enriches data with detailed information on malware both pre- and post-infection to conduct forensics on infiltrated endpoints. Its unique guided interface provides helpful guidance, best practices and suggests the next logical steps for security analysts.
- Automate investigation with minimal interruption to end users
- Automatically defuse and block threats, allowing security analysts to hunt on their own time
- Patented code-tracing technology delivers full attack chain and stack visibility even if the device is offline
- Preserve memory snapshots of in-memory attacks for memory-based threat hunting
- Guide interface displays clear explanations why the event is flagged as suspicious or malicious, lists corresponding MITRE attack framework, as well as logical next step for forensic investigation






